Born from warfighter requirements and inspired by the animal kingdom’s natural defense mechanisms, we developed patented, quantum-resistant Data Camouflage™ technology for data in motion—safeguarding enterprises and the individuals who depend on them.

When data is set into motion–traversing through untrusted networks–is when it’s most vulnerable to attack.
And legacy solutions like SD-WAN and VPN simply don’t provide the level of security required to protect data in motion for a post-quantum world.
Yet existing data security architectures focus almost exclusively on data at rest and data in use.

When data is set into motion–traversing through untrusted networks–is when it’s most vulnerable to attack.
And legacy solutions like SD-WAN and VPN simply don’t provide the level of security required to protect data in motion for a post-quantum world.
Yet existing data security architectures focus almost exclusively on data at rest and data in use.
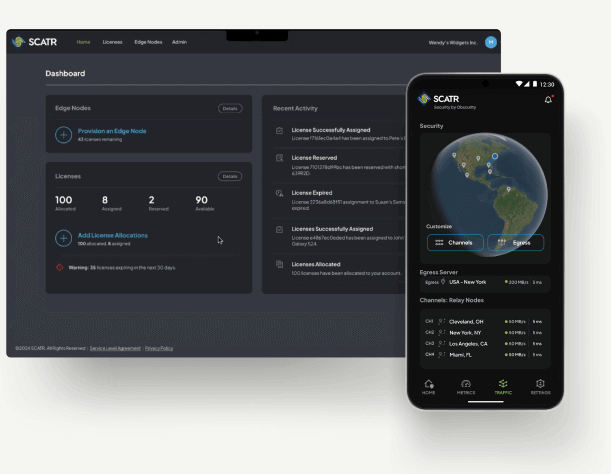
The STUN™ security platform empowers organizations to proactively secure data in motion across untrusted networks, providing data obfuscation, resiliency, and quantum-proof security. Our patented, quantum-resistant Data Camouflage™ technology allows enterprises to secure their data in motion across the world’s most hostile environments, addressing a critical gap in Zero Trust security architectures that often focus on protecting data at rest and data in use.
SCATR Delivers Zero Trust Transit™ security for data in motion.